Choosing the Safest Browser
Category:Information Security,Infosec Communicator,Internet Safety,UncategorizedThere’s always discussion among techies about which internet browser is better. Most of them end up bashing Internet Explorer. Does it really matter which browser you use?
Maybe, but not for the reasons you might think. Here’s a list of the five most common browsers, in no particular order:
- Opera
- Firefox
- Safari
- Internet Explorer
- Google Chrome
Which of these browsers is the safest? The one with the fewest number of reported vulnerabilities? I asked my Cyber Self Defense class last quarter to guess which browser had the most vulnerabilities.
Here’s the order they came up with:
- Internet Explorer
- Safari
- Opera
- Firefox
- Chrome
According to the Symantec 2008 Internet Threat Report, here’s the list of browsers ranked from most reported vulnerabilities to the least:
- Firefox
- Internet Explorer
- Safari
- Opera
- Chrome
Is this the order you expected? Did you think that Internet Explorer would have the highest number? If we go strictly by number of vulnerabilities reported, Google Chrome would be the safest browser to use and Firefox the worst.
Another way to look at browser safety is how long it takes for a reported vulnerability to be fixed. How would you rank these same five browsers from shortest to longest patch time?
Again, the class assumed the worst browser would be Internet Explorer. However, Safari had an average “exposure” time of nine days, compared to the “best,” Firefox, which normally took only one day to patch.
Internet Explorer is attacked the most. Why? Because it’s used by the most people and provides a higher ROI for cyber criminals. Because it’s attacked the most, it MAY be safer to use a different browser. However, safer Internet browsing has as much to do with safe practice as it does browser choice. If you browse unsafe sites, you’re more likely to be attacked.
Here’s what we’re telling students, faculty, and staff at the Rochester Institute of Technology about safer internet browsing.
Browser Security
How can you tell how secure your web browser may be? Scanit’s Browser Security Test checks your browser security settings and provides a report explaining the vulnerabilities, the potential impacts, and how to correct them.
Update Regularly
It is important to keep your browser up-to-date on security patches. This can typically be done from within the browser, or directly from the vendor’s website. Check for updates at least monthly.
Anti-Phishing Tools
Internet Explorer 7.x and higher, Safari 3.2 and higher, and Mozilla Firefox 3.x and higher all provide some protection against phishing.
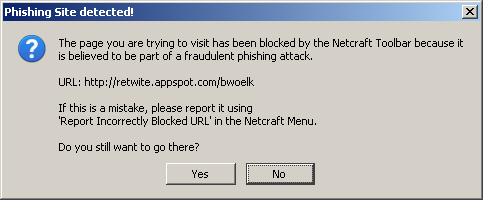
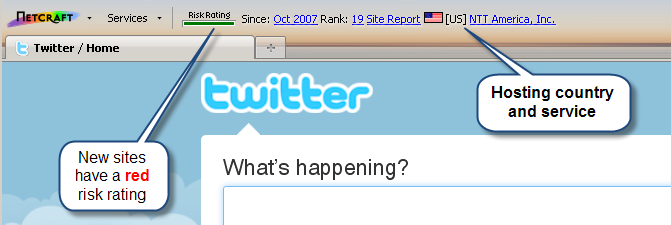
The Netcraft Toolbar is a browser plug-in available for Internet Explorer and Firefox. The toolbar helps stop phishing attempts by blocking known phishing sites and providing hosting information about the sites you visit.
The McAfee Site Advisor is a browser plug-in available for Internet Explorer and Firefox. The Site Advisor warns you of websites known to have malicious downloads or links by checking them against a database at McAfee.
Limited Account Privileges
Limiting account privileges provides simple but effective protection when working online. Limited accounts allow you to do most daily activities but do not allow you to install software (only accounts with administrative privileges can install software on the computer).
Many attacks take advantage of administrative privileges to install malware on your computer. If you’re using a limited account, attackers and malicious websites will not be able to install malware. (This is less of an issue with Windows 7 and Mac OS X because they ask you to confirm software changes.)
Ben
Postscript: I’ve included links below to my 6/30/11 posts updating this article.
Related articles
- Updated: Choosing the Safest Browser, Part One (benwoelk.wordpress.com)
- Choosing the Safest Browser, Part 2 (benwoelk.wordpress.com)
- Avoiding Phishing (benwoelk.wordpress.com)