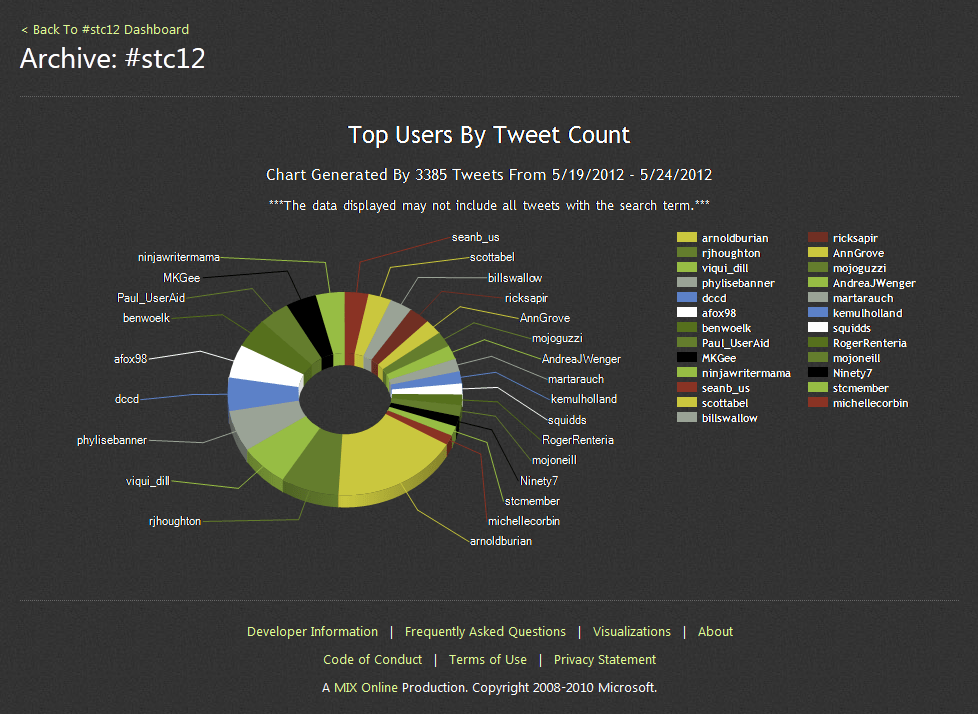
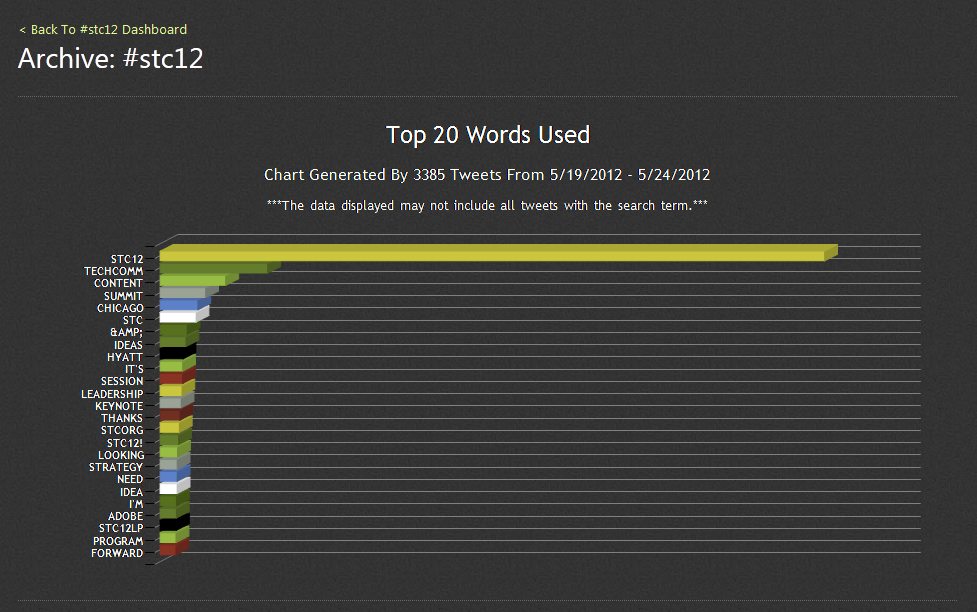
RIT InfoSec Awareness: an Interview With Ben Woelk
Category:EDUCAUSE,Facebook,Higher Education,Information Security,Infosec Communicator,Internet Safety,Social NetworkingRIT InfoSec Awareness an Interview With Ben Woelk.
Read my interview with RIT alumnus Neil DuPaul on the Veracode Blog where we discuss how we’re increasing information security awareness at the Rochester Institute of Technology. What do you think of the cards?