Beware of Good Ole Scammer Claus
Category:Information Security,Infosec Communicator,Internet Safety,Privacy,RiskI’m sharing the contents of an advisory I sent out to the RIT community regarding holiday scams and phishing attempts. I think you’ll find the information helpful.
 Beware of Good Ole Scammer Claus!
Beware of Good Ole Scammer Claus!
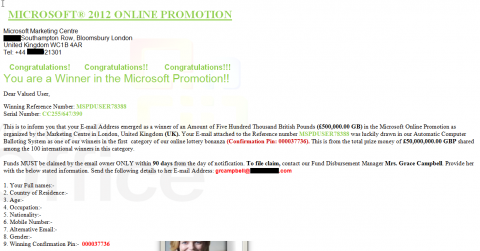
As we head towards our holiday break, remember that there are many scammers trying to trick you into revealing credit card numbers and other Private information–information that can be used for Identity Theft. As part of their attempts, we’re seeing an increase in phishing attempts–some disguised as delivery confirmations.
Follow these guidelines to help ensure your Private information (and your money) stays secure on the Internet.
Use a Secure Computer
- Make sure your computer meets the RIT Desktop and Portable Computer Standard before going online.
- Don’t use public computers to send private information over the Internet.
Use Strong Passwords
- Use a strong, unique password or passphrase where allowed. See our How to Create a Strong Password brochure for tips on choosing strong passwords.
- Take advantage of any additional security features offered by your bank.
Be alert for phishing and scams
- Never respond to an e-mail requesting that you reply with your login information. Scammers go to great lengths to make e-mails appear genuine, but no legitimate bank or retailer will ever ask you to submit private information by e-mail.
- Never give out a bank account number to anyone, and be wary of anyone who insists upon cash or wire transfer only.
Research the Company and Website
- Investigate any retailer you are considering using. How trustworthy are they?
- Check the company’s privacy policy.
- Check for negative reviews using a search engine.
- If you’re shopping at an auction site, check out the seller’s feedback.
Make Sure the Website Uses Encryption
- The address bar should begin with https (not just “http”) and there must be a padlock in your web browser (the location varies by browser, it usually appears in the address bar or the status bar at the bottom).
Monitor Your Accounts
- Keep track of all your purchases and account history from start to finish and beyond.
- Save copies of your orders and receipts, as well as e-mail confirmations and product descriptions.
- Follow up on your purchases by monitoring your bank account and credit card statements for any unauthorized transactions.
- You may also want to check your credit report annually (check for free at www.annualcreditreport.com).
Problems and Complaints
Identity Theft
- If you think you have been a victim of identity theft, take action immediately.Contact your card issuer and follow their instructions.
- New York State Identity Theft – ID Theft Kit https://www.ag.ny.gov/sites/default/files/pdfs/publications/ID_Theft_Kit_2011.pdf
- Federal Trade Commission – Recover From Identity Theft https://www.consumer.ftc.gov/features/feature-0014-identity-theft
Online Shopping Complaints
- If you think you have been a victim of online shopping fraud and/or cannot resolve a problem with the seller, contact the following agencies:
- NYS Attorney General’s Office Consumer Complaint Form https://www.ag.ny.gov/internet-bureau-online-complaint-form?a=CF
- Better Business Bureau https://odr.bbb.org/odrweb/public/GetStarted.aspx
Additional Links
- Online Shopping Tips
- Phishing Tips
Have a good (safe) holiday!