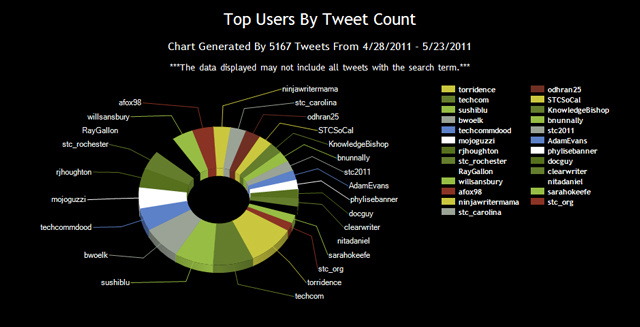
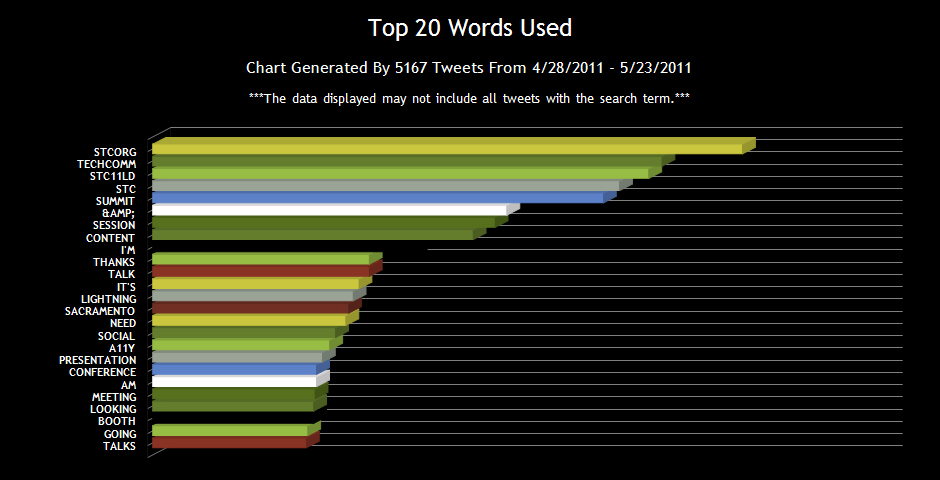
Updated: 2012 Speaking Schedule, January through June
Category:EDUCAUSE,Higher Education,Information Security,Infosec Communicator,Internet Safety,Presentations,Social Networking,STC,STC Rochester,SummitI’ll be speaking at the following events this winter and spring. Watch for my presentation materials on SlideShare.
January 9: HEISC (Higher Education Information Security Council), Town Hall. Recording available.
January 30: Bullet Proofing Your Career Online (with Hannah Morgan, @careersherpa), ABCPNG (Always Be Connecting Power Networking Group), First Unitarian Church, Rochester, New York
Description: What are the 10 key steps to building and securing your online reputation? A security professional and a career sherpa provide their perspectives on how to create an online presence that enhances and promotes your career safely and effectively.
April 23rd: Bullet Proofing Your Career Online (with Hannah Morgan, @careersherpa), STC Rochester Spectrum Conference, Rochester Institute of Technology, Rochester, New York
April 24th: Leadership Day, STC Rochester Spectrum Conference, Rochester Institute of Technology, Rochester, New York
Facilitating the event and the panel discussion
May 17: Engage! Creating a Meaningful Security Awareness Program (with Cherry Delaney, Purdue University), EDUCAUSE Security Professionals Conference 2012, Indianapolis, IN
Abstract: This session will help attendees identify available resources and tools and determine the steps needed to create an engaging security awareness program. We’ll share how to integrate social media, video and other resources in an effort to reach a variety of audiences. We’ll also discuss how to leverage security incidents to create opportunities for engagement with your community. We’ll conclude the session by helping you plan a series of targeted activities for a high profile event such as the National Cyber Security Awareness Month.
May 20: Communications Liftoff! Rocketing your Community to the Stars, Leadership Day progression, STC Summit, Rosemont, IL
May 21: Bullet Proofing Your Career Online (with Hannah Morgan), STC Summit, Rosemont, IL
May 23: Shockproofing Your Use of Social Media 2012, STC Summit, Rosemont, IL



 It’s been a little less than two weeks since the
It’s been a little less than two weeks since the